Eclipse Attack
Eclipse Attack
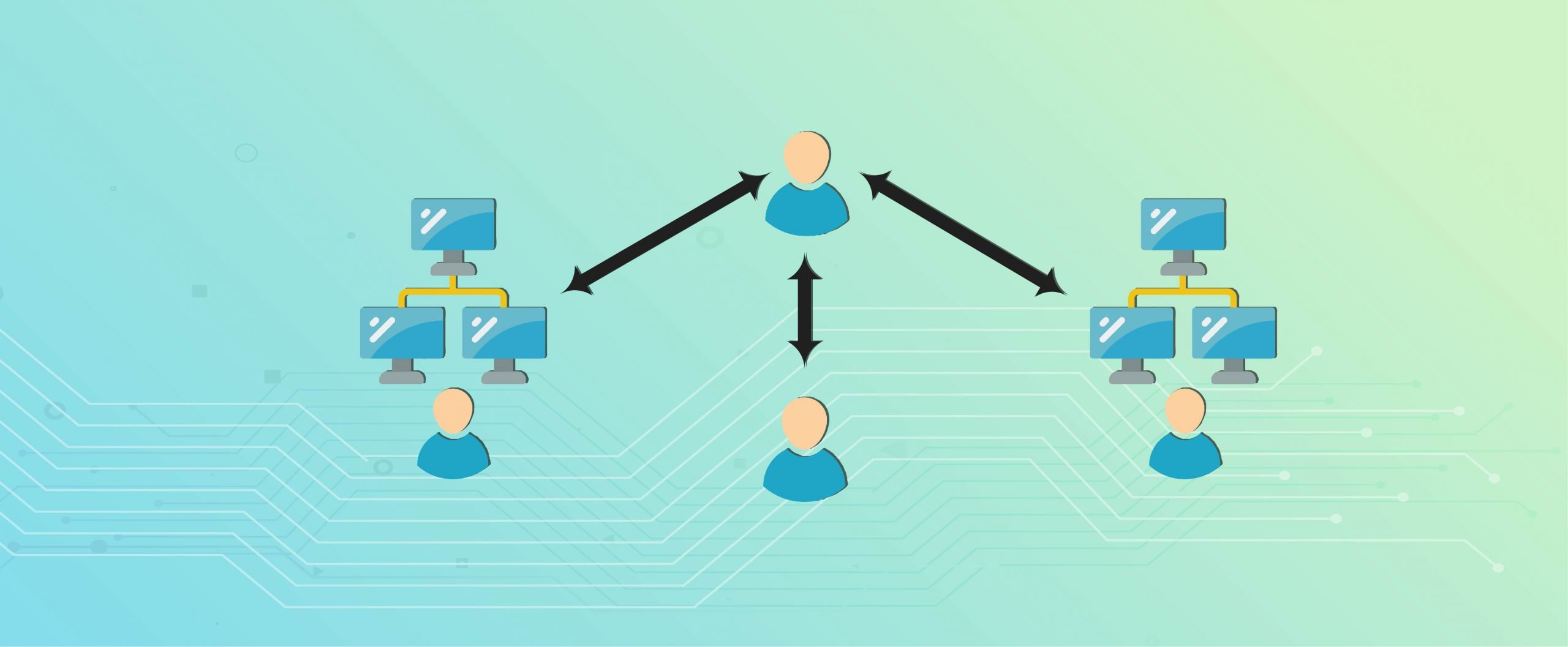
- Eclipse attacks include the isolation of a hostile actor in a peer to pair (P2P) network from a single user or node. If an eclipse assault is carried out, the attacker tries to transfer inbound and outgoing connections to attacker-controlled nodes from the target user's genuine adjacent nodes, shutting the target off in a completely different environment from actual network activity.
- The attackers' ability to control the isolated node can lead to fraudulent transaction confirmations and to block mining interruptions by overloading the genuine present condition of the blockchain ledger.
- The ability of such attacks to be effectively carried out depends significantly on the underlying structure of the target blockchain network.
- Such assaults rely on the use of a target nearby nodes. The ability of such attacks to be effectively carried out depends significantly on the underlying structure of the target blockchain network. Such assaults rely on the use of a target nearby nodes.
How Does It Work?
- Bitcoin miners require specialist equipment to produce new blocks, while, nodes with minimum computer power that are nonmining (or full) are easy to run. This helps to decentralise Bitcoin, as everyone may move a node on a low-specific hardware. The programme keeps the transaction database, which it syncs with its near colleagues to stay locked with the network.
- For many nodes, bandwidth is a limiting constraint. Although there are a huge number of devices that operate the software, because of restrictions in Bitcoin software the ordinary device does not connect to many devices directly (which only permits a maximum of 125 connections).
- When an eclipse attack is perpetrated, the malicious actor ensures that all the connections to the target nodes are formed. Initially, the company would inundate the target with its own IP addresses to which the victims may connect when their software is restarted. Either a restart (i.e. an attack by the DDoS on the target) may be forced, or an attacker can just wait for it.
- After this, the unwary victim is at the expense of the rogue nodes — the attacker cannot feed erroneous data without viewing the wider network.
Top Case Studies You May Like